The long-standing Ursnif trojan is back in a new form to infect computers and steal personal information, all via a Microsoft Word document.
To begin, we’ll repeat a warning we’ve been making for years …
No .doc files
DO NOT open .doc files from any source (not .xls or .ppt either).
Most infected and dangerous Word documents use the old ‘.doc’ format which was replaced over a decade ago. Ursnif is just one of many nasties that need .doc format.
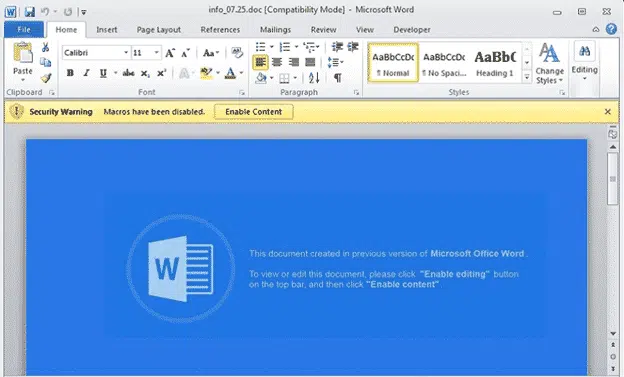
The new form of Ursnif Trojan tries to trick people into running the dangerous macro code by clicking the ‘Enable Content’ button.
The document admits that it’s the old .doc format and falsely claims you need to click the ‘Enable Content’ button to view the document.
Source: Fortinet
“ This document created in previous version of Microsoft Office Word.
To view or edit this document, please click ‘Enable editing’ button on the top bar, and then click ‘Enable content’. “
In technical terms, this is known as ‘Bulls%$^t’.
Inside Ursnif
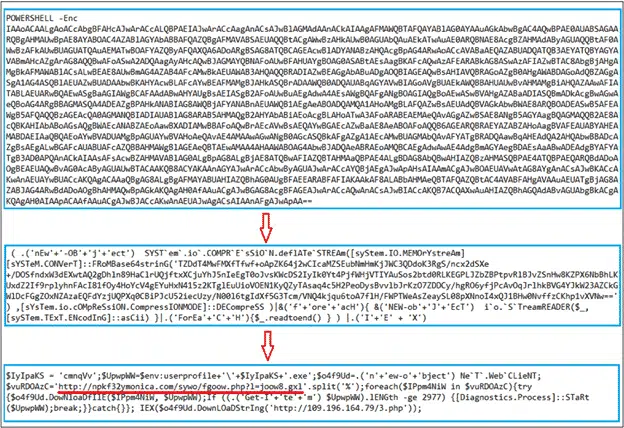
These new attacks have sophisticated code to hide from anti-virus software. Here’s just one example. The top section is Base64 encoded text in a Word form. Decode that to produce even more Base64 encoded text in the middle section.
Source: Fortinet
Only more Base64 decoding shows the real code that’s run including the web link.
The main payload isn’t included in the document at all. The Word macros grab malicious code from the Internet. When that code is run, it collects your personal data then sends it out to criminals.
If you’re interested in the nerdy details of a modern Word macro virus, Fortinet has a long explanation.
Office exploits have come of long way from simple, easy to read, code. In those days, Microsoft tried to dismiss the whole problem by calling them ‘prank macros’, as if infected Office documents could not do any harm.
Word’s Melissa virus is 20 years old – what’s changed?
Make your own Word virus for $40
Fake OneNote/Sharepoint emails try to steal your password