A Word document and a floppy disk caught a serial killer back in 2010. There are still lessons for anyone wanting to keep their personal or business data confidential.
Known as the ‘BTK killer’, he murdered 10 people in Kansas between 1974 and 1991. The murderer was finally caught in 2004. He liked sending notes to the police and public but made the mistake of switching from paper to a floppy disk (photo below to help younger readers <g>).

On the floppy disk was a Word document with BTK’s latest missive. He didn’t realize that the disk also had other ‘deleted’ files.
Computer forensics experts examined the disk and found other Word documents. Those documents had been ‘deleted’ but still available. Enough of the older documents remained for them to get a first name and location where a document was made. That ‘meta data’ from the deleted document was enough to track down the killer.
That was over a decade ago, but the privacy lessons still apply.
Computer Forensics is for everyone
Even though floppy disks are virtually unknown now, the principle still applies to USB memory sticks, some optical disks and hard drives. All can have remnants of deleted files and documents.
Terms like ‘computer forensics experts’ make it sound very complex and specialist work. It can be complicated, but the basics are available to anyone.
‘Deleted’ files can be read by ordinary people with no training or qualifications.
Recovering deleted files from a USB memory stick (the modern floppy) is possible by anyone. There are many tools that can do that.
Examining a disk at a detailed level (to find fragments of a deleted file) can be done by anyone. It can be time-consuming but not beyond any reasonably competent person.
Deleted Files are still there
Computer programmers are always focused on safety of data and speed. That means a ‘delete’ option doesn’t truly remove the data.
‘Delete’ simply hides the file and free up the space to be overwritten in future. Nothing is truly removed.
To truly erase data, you need to ‘Wipe’ a drive or disk. Our ebook Beating Bots, Spies and Cockups includes a whole chapter on wiping drives and truly deleting files. Also, options to wipe free disk space only and how to see for yourself that a drive has been wiped.
Don’t forget the hidden document info
The criminal was traced from the hidden info in the Word document (meta-data) not the content of the document itself.
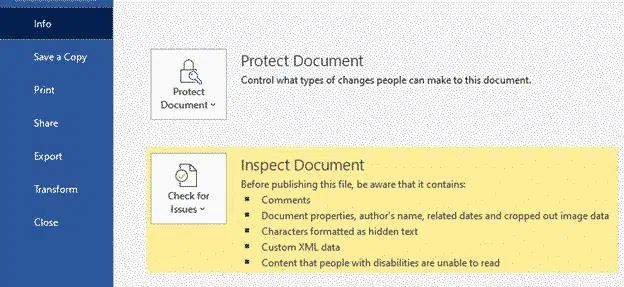
These days, Microsoft has somewhat addressed this with the Info | Inspect Document option which checks for some unseen details in documents and removes them.
* We follow the admirable modern practice of NOT naming serial killers. Those people often crave attention they don’t deserve.