Microsoft has disclosed and fixed a ‘zero-day’ security bug in Publisher. It’s a “Security Feature Bypass” that’s already being used to infiltrate computers, is so incredibly simple and should never have happened at all.
Called CVE-2023-21715 “Microsoft Publisher Security Features Bypass Vulnerability” it easily allowed macros to be run in Publisher when they should not.
What’s the security bug?
It relates to Microsoft’s security feature called “Mark of the Web” or MOTW which tags files from Internet sources. When opened in Office apps, MOTW tagged files can’t run any macros.
Did we say “Can’t” run macros? … better to say “Should not” run macros. That’s because Publisher breaks Microsoft own MOTW rules by offering an “Enable Macros” button.
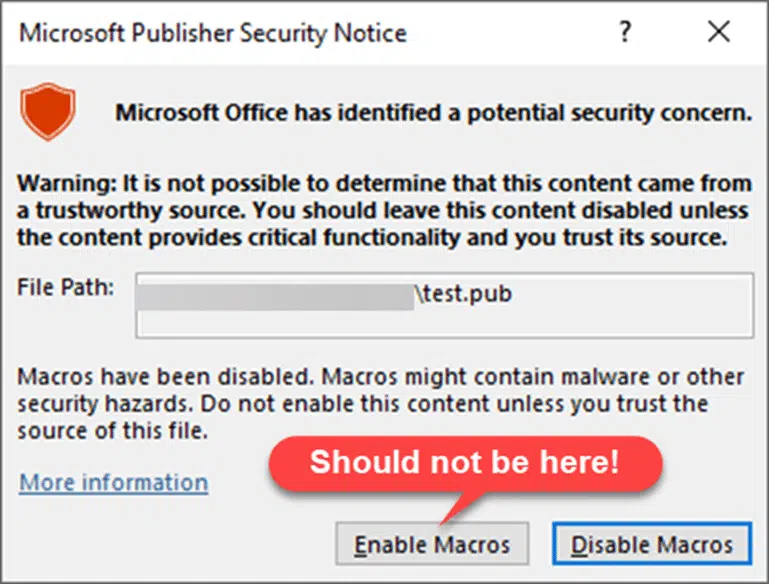
Since the rushed update to Publisher 365, the Microsoft Publisher Security Notice now has only one choice ‘Disable Macros’ which is how it should have been for a long time.
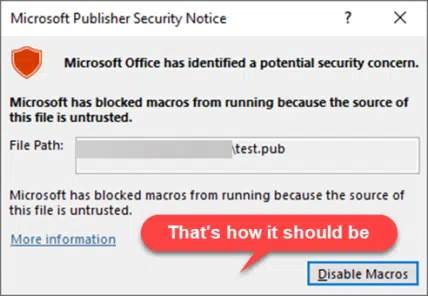
Remove the MOTW tag and .PUB can be opened in Publisher with an ‘Enable Macros’ button.
Publisher has no Protected View
Having an ‘Enable Macros’ button is made worse because Publisher doesn’t have the same Protected View option that’s in modern Word, Excel and PowerPoint.
If a hacker can trick someone into allowing macros to run, there’s no other defence available in Publisher. In the other Office apps, a customer has to both go out of Protected View and enable macros.
Sadly, Microsoft has ignored security concerns about the missing Protected View for Publisher. Astonishingly they said it was ‘not a vulnerability’ and shunted it off as a ‘Feature Request’ (which is Microsoft code for ‘Ignore’).
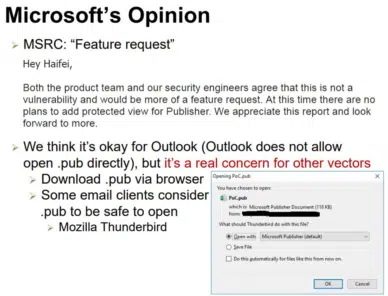
Where was Microsoft’s Security and Testing?
Mark of the Web has been in development for years and was implemented in mid-2022.
How in hell did this lapse bypass any security or general testing at Microsoft? Was there any security or general testing done at all? It’s not an obscure or difficult issue. Checking that Office apps obey MOTW should be one of the first and basic pre-release checklists, but apparently not.
It’s beyond understanding how this could happen. Didn’t Microsoft’s testing system detect this sooner? Or maybe they did notice but took no action until hackers started using the lapse to infect computers?
Whatever the reason, it’s a black mark against Microsoft. Keep it in mind next time Microsoft execs parrot their line about security being a top priority?
What must you do?
If you use Publisher 365 then update your computer asap. Microsoft released an update on Valentines Day – 14 Feb 2023 which fixes the Publisher security bug plus two other lapses in Word and Office generally.
The security report only mentions Microsoft 365 apps but the 14 Feb patch list also covers Office 2021, LTSC, 2019 and 2016. We’re inclined to recommend getting updates for any of those versions as well.
In any Office for Windows app go to File | Account | Office Updates | Update Options | Update Now.
Credit where it’s due
Haifei Li https://twitter.com/HaifeiLi has a good thread on this security bug.
More VBA macro blocks coming to Office, details
Inside the Office VBA/MOTW changes