Criminal have found another way to (mis)use Microsoft Office and infect computers using the latest ‘zero-day’ hack.
You may know that Adobe’s Flash was a popular add-in for web pages to display multi-media content. But Flash was very insecure and unstable so it’s been mostly replaced with other secure systems. Most modern browsers block Flash content by default and you’re rarely prompted to install Flash.
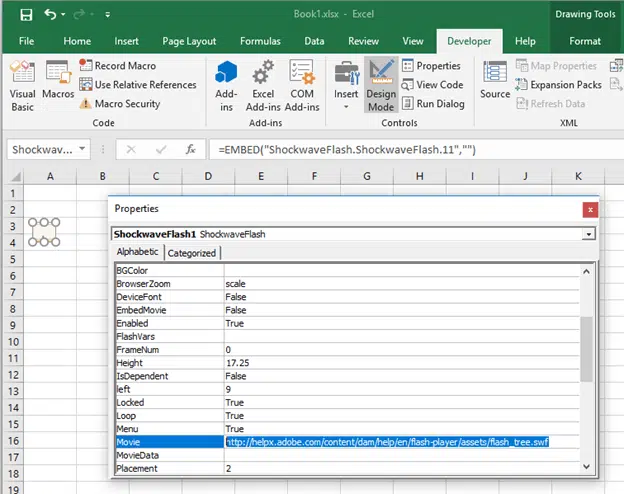
Guess which popular software still allows links to Flash content …. you guessed it, Microsoft Office.
The latest hack takes advantage of that security hole. An infected Office document has a link to Flash content which is downloaded and run to gain access to the computer.
Source: IceBrg.io
The sneaky smarts behind this trick is that there’s nothing really suspicious in the Office document. All the nasty code is in the Flash component that’s downloaded and run within Office.
All the hackers need to do is trick people into opening and activating the document. That means fooling people into opening the doc completely and not just in Protected Mode.
Pass the buck
Microsoft moved quickly, after the proverbial horse has bolted, to release an information page. That page, in usual Microsoft style, is factually correct but also misleading and designed to shift the blame elsewhere.
A casual reader of ADV180014 would think this is an Adobe Flash bug and nothing to do with Microsoft at all.
There’s the usual talk about Mitigating Factors before you get to the crucial information under ‘Workarounds’. More on that below.
Office 2016 for Windows
Office 2016 for Windows, Office 365 has now blocked Flash, Shockwave and Microsoft’s own Silverlight by default but only for Monthly Channel starting this month (June 2018).
Users of previous Office 2016 Windows/Office 365 builds do NOT have this default block. The ‘Semi Annual Targeted (SAT) Channel’ is getting a default block in September 2018. ‘Semi Annual (SA) Channel’ users wait until January 2019.
Microsoft has details of how to bypass the blocks on this poorly documented page. The page says that the blocks are in “new builds of Microsoft Office for Office 365” but the page is undated nor is there a build number specified. It also isn’t specific about Office for Windows or Office for Mac but since the fix uses the registry, you can infer that it’s Office for Windows.
There’s no mention of Office 2016 for Windows, perpetual licence version. Was the Flash/ShockWave/Silverlight block added in a build? Paying customers deserve to know.
Office 2010 and Office 2007
If you dig down into Microsoft’s ADV180014 you’ll find ways to block Flash content from Office 2010 and Office 2007.
Use this information to edit the registry or make a .reg file to do the job on multiple machines.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\ActiveX Compatibility\{D27CDB6E-AE6D-11CF-96B8-444553540000}] "Compatibility Flags"=dword:00000400 [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\ActiveX Compatibility\{D27CDB6E-AE6D-11CF-96B8-444553540000}] "Compatibility Flags"=dword:00000400
Those two registry changes are supposed to block Flash from running from any program which honors those registry settings – which includes Office 2007 and Office 2010. However that appears to conflict with other advice from Microsoft on other pages.