The US National Security Agency (NSA) discovered a serious security bug in Windows and, for the first time, told Microsoft so the company could fix it. That bug could also affect Microsoft Office or other programs. It’s important to update your Windows 10 asap, that’s not our opinion, it’s the US government.
The NSA found a bug in the core Crypto API (crypto.dll) which allows digital certificates to be faked. Certificates are used to sign or verify the content and source of documents, emails, code and programs. Even common https secure web pages could be affected.
In Office, some security settings allow digitally signed documents or code to be run without prompting. Trust Center | Macro Settings has an option to run digitally signed code without warning. Happily, it’s not the default setting (that’s Disable all macros with notification).
A digitally signed document is presumed to be legitimate and safe so any way to fake that identity check is a very big deal.
Imagine the ‘fun’ hackers and criminals could have if they could send out documents that appear to come from within your organization, signed from a government agency or Microsoft itself!
While the bug hasn’t been exploited, it’s only a matter of time before hackers start using it to trick people and infect computers.
Security Bug Fixes
Only Windows 10, Windows Server 2016, 2019 and some Server Core installations are affected.
While Microsoft takes their usual ‘hide the bad news’ approach, the NSA itself has a stark warning to all Windows users:
“The consequences of not patching the vulnerability are severe and widespread.
Remote exploitation tools will likely be made quickly and widely available.
Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners.”
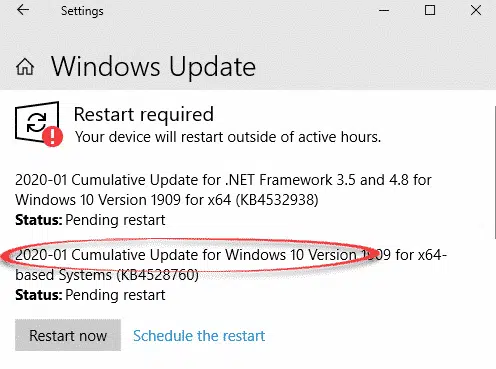
Patches are now available and in most cases they’ll be installed automatically. We checked our machines and they had been updated and restarted overnight except one.
The KB reference number depends on your Windows version. Look for an update called ’2020-01 Cumulative Update for Windows 10 ….’.
If you have disabled or paused Windows updates (a legitimate choice), this is one of those situations where applying the specific patch listed here or allowing a full update would be wise.
It’s great that the NSA decided to tell Microsoft about this security bug. In the past the US government has kept this information secret, only for it to leak out and be exploited by hackers.
Let’s hope this latest disclosure represents an ongoing change in NSA policy, not a one-off anomaly.
The full story
Office Watch has often mentioned that it’s in Microsoft’s interest to downplay the severity of security bugs in their products and obscure the details.
As a great example, compare Microsoft’s vague CVE-2020-0601 notice and the waffling blog post: January 2020 Security Updates: CVE-2020-0601. The blog post is mostly boasting Microsoft’s various security partnership acronyms like CVD and SUVP with no detail about the bug itself.
Given Microsoft’s self-interest, it’s not surprising that they have only rated this Windows bug as ‘Important’ not the higher Critical level it probably deserves.
Compare that with the detailed and stark report from the NSA itself. Their Cybersecurity Advisory is clear about how widespread this Windows security bug could be and why fixing Windows is essential.
“NSA assesses the vulnerability to be severe and that sophisticated cyber actors will understand the underlying flaw very quickly and, if exploited, would render the previously mentioned platforms as fundamentally vulnerable.”
“ Exploitation of the vulnerability allows attackers to defeat trusted network connections and deliver executable code while appearing as legitimately trusted entities. Examples where validation of trust may be impacted include:
- HTTPS connections
- Signed files and emails
- Signed executable code launched as user-mode processes “
“ NSA recommends system owners prioritize patching endpoints that provide essential or broadly replied-upon services. Examples include:
- Windows-based web appliances, web servers, or proxies that perform TLS validation.
- Endpoints that host critical infrastructure (e.g. domain controllers, DNS servers, update servers, VPN servers, IPSec negotiation). “
The NSA also includes some technical details so IT gurus can check certificates while systems are being updated.