A detailed look at a common email phishing attack, what to look for and how to avoid it.
The most common form of phishing (password stealing) attack fakes a Microsoft account login. Most people have a Microsoft account for their work, home or both so it’s a large slow-moving target for criminals.
Here’s an email that was passed along to us, the ‘payload’ is in the HTML file, intended to be opened in your browser.
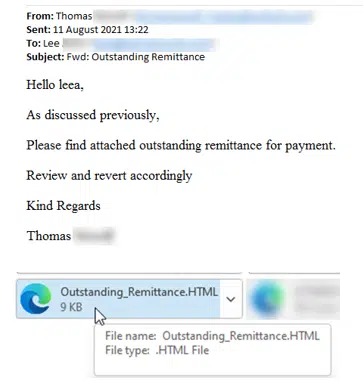
Of course, there’s no ‘Outstanding Remittance’, just a tricky way to get your Microsoft account details.
If you clicked on the attachment to open it, this is what you might see. A sincere looking but fake Microsoft 365 login page.

ALERT: Any savvy computer user would NOT open a .htm or .html attachment unless they checked with the receiver that it was legitimate.
“Trust no-one” or beware ALL attachments
A common refrain from Microsoft is to be wary of email attachments from unknown sources. That’s reasonable advice, up to a point. Really you need to be wary of any incoming attachments, even from people you know.
That especially applies to insecure and commonly hacked file formats like .htm .html and the old Office formats .doc .xls .ppt etc.
Our example shows why you should not trust insecure attachments, even from known ‘trusted’ sources.
The senders email account had been hacked and used to send the phishing emails to people in his contact list. That’s how the email, above, has the name as well as email address of the receiver. Some spelling mistakes are a clue to a possible fake.
Social Engineering
These emails can take many forms, called ‘social engineering’ in the trade. Trying to trick you into opening an attachment by making it look real and urgent.
Obfuscation
You might wonder why security software from Microsoft or others doesn’t protect you from attachments like this. The answer is ‘obfuscation’, the web page attachment is deliberately confusing to hide the true intention from security scanners.
Instead of a simple link to an online web page, the .html attachment looks like this:
A long complex JavaScript string hides the malicious code.
How to protect yourself
Two-factor authentication is essential for everyone. It’s the single best thing you can do to protect yourself. Even if a hacker manages to get your login password, it’s useless without the second, time-limited code.
‘2fac’ is now so common it’s being recommended by John Oliver on the HBO show, Last Week Tonight.
Be very wary of any incoming files using the older, insecure, file formats. Especially the old Office files with three letter extensions (.doc .dot .xls etc) and any web page format (.html .htm .asp etc).
The Myth about Two-Factor Authentication
Why Old Office documents should be banned